Improving Privacy and Security in Decentralizing Multi-Authority Attribute based Encryption
ABSTRACT:
To protect cloud storage, many design based on attribute-based encryption are offered, however the majority of them focus on data content privacy and access control, with less emphasis paid to privilege control and identity privacy. Data sharing in the cloud is very feeble to cyber-attacks since data stored on cloud servers, and multiple users access data from unknown servers, resulting in Data security and privacy as critical issues for remote data storage. The study is built on the uncertainty of data privacy and user integrity.
Existing System
Cloud computing does not encrypt confidential company data. Security issues in User Data. Expensive storage price. Data’s are not in encrypted format. Lagging in data security. One of the primary issues about cloud computing security and privacy is data protection.
If cloud computing security and privacy are ignored, each user’s private information is put at risk, allowing easy cyber breaches to break into the system and abuse any users’ private storage data
DISADVANTAGES
- The information is not encrypted.
- Lagging in data security.
- Expensive storage price.
- Security issues in User Data.
- Cloud computing does not encrypt confidential company data.
Proposed System
Confidential corporate data are encrypted in cloud computing. Virtualized environment in Cloud Computing platform Online Storage for Data Handing user data in the virtualized platform in a highly secure way Cost-Effective, Pay peruse. Avoid storing sensitive information in the cloud. Read the user agreement to learn how your cloud storage works. Be serious about passwords Encrypt. Use an encrypted cloud service.
ADVANTAGES
- Avoid storing sensitive information in the cloud.
- Read the user agreement to learn how your cloud storage works.
- Data Storage Online, Passwords should be taken seriously.
- Encrypting confidential company data on the cloud is computing.
- Use an encrypted cloud service.
Hardware Requirements:
Speed : 2 GHz core CPU.
RAM : 4 GB RAM or above.
Hard Disk : 120 GB HDD.
Processor : Intel i3 and above processor.
Software Specification:
Public Cloud account : AWS
Operating System : Windows/Linux OS
Front End : KMS Key Encryption
Back End : Amazon Web Service
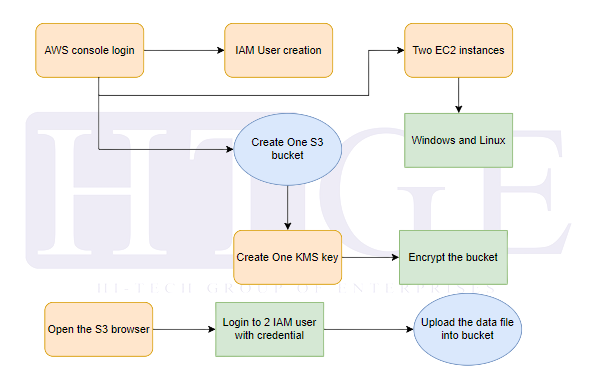
Flow Diagram