Welcome to Hi-Tech's Freshers Pool

Welcome to the Hi-Tech group of Enterprises’s Fresher Pool Page. We are providing Online and Offline classes in Programming, Cloud, Operating systems, and Digital Marketing.
Hi-Tech Group of Enterprises has expanded its services into three distinct sectors. Hi-Tech Group of Enterprises is one of India’s leading IT corporations. Our corporate headquarters are in Pondicherry, India. With client satisfaction, we give our finest services in all four of our verticals.
Choose Your Interest



- AWS (Amazon Web Services)
- Microsoft Azure
- Google Cloud
- DevOps
- Kubernetes
- Cisco

- Console Application
- Web Application
- Cloud Projects

- SEO Services
- Social Media Marketing
- Web Designing
- Branding Products
- Online Promotions
Projects
Food Wastage Application In Django with Source Code
Project:This Food Waste Management service can assist in collecting the leftover food from single users and restaurants to distribute among those in need. This project is used to manage waste foods in a useful way.Every day people are wasting lots of food.

Centralized Hospital Management System In Java with Source Code
Project:This project is mainly designed for the Indian hospital and Health care industries. Private and government-based hospitals both equally get benefited from this application. In Indian history, the transcriber has not been able to download the Doctor’s voice videos.
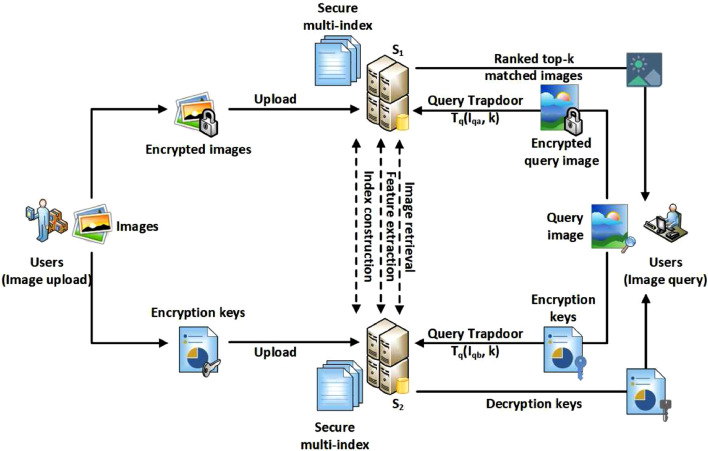
Privacy-Preserving Content-based image retrieval (CBIR) applications
Project:Privacy-Preserving Content-based image retrieval (CBIR) applications have been rapidly developed along with the increase in the quantity, availability, and importance of images in our daily life. However, the CBIR scheme’s widespread adoption has been hampered by its high processing and storage needs.
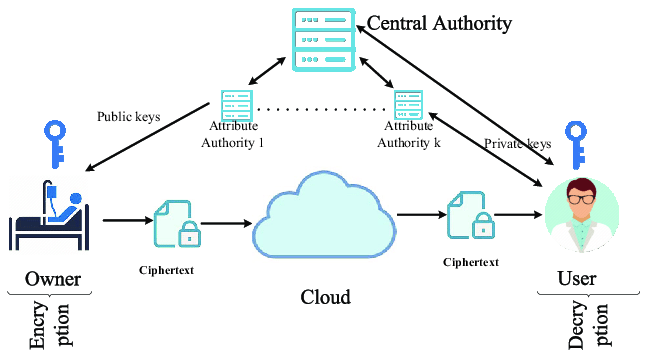
Improving Privacy and Security in Decentralizing Multi-Authority Attribute based Encryption
Project: To protect cloud storage, many design based on attribute-based encryption are offered, however the majority of them focus on data content privacy and access control, with less emphasis paid to privilege control and identity privacy.The study is built on the uncertainty of data privacy and user integrity.




